Over the course of the past few years, you may have noticed there have been an increasing number of news stories and media coverage of companies experiencing data breaches, with names, passwords, addresses, and more being exposed. Many of these targets have been big, well-known companies, including financial institutions, e-commerce, cloud storage and social media companies. These attacks have cost companies financially, and reputationally - not only did they lose millions of dollars, but damaged a large portion of their customer’s trust. Would you continue to shop at store or use a product if you weren’t confident they kept your personal information secure?
So, how does this happen? It could be a planned attack on a network, targeting weak passwords and encryption, access being left open to files that are unsecured, or an “inside person” pulling off a heist with a flash drive, but most often, it’s caused by phishing - an unsuspecting employee with access to sensitive data, opening an email with a malicious attachment or clicking through to a malicious URL via email or on a website. According to a digitalguardian.com article, 91% OF CYBER ATTACKS START WITH A PHISHING EMAIL!
Not only are these “top targets” at risk, but any institution that keeps these types of records is susceptible to attack - including Higher Educational institutions such as ours. Every day, hundreds of our employees handle personal records and use computers and devices that contain access to this information. As such, it is extremely important for all members of our community to be aware of what phishing is, and to follow best practices to identify and validate the authenticity of the email, and avoid being phished.
WHAT IS PHISHING?
Phishing is a malicious attempt to lure an authorized user to share information - this is typically done via email or web site links or redirects. A phishing email will typically have:
- A subject line proclaiming urgency - may include your name and a warning, scare tactic, or invitation to accept a prize
- A “From” field containing someone you know or a company you know. This information may be “spoofed” - that is, fabricated so that it looks like it’s coming from that person/company, but if you check closely, you can see that it’s not.
- A File/attachment as a .zip file, .exe file, or other type of file you are not familiar with
- Hyperlink spoofing a familiar website - prompting you to click there to log in.
- Body that may use inconsistent language, include typos and grammatical errors.
- No signature or a different signature than you would normally see in an email coming from that person.
PHISHING EXAMPLES:
Below is a classic example of a spoofed email directed to an amazon.com customer. Note that the “From” field contains the company, but checking closely, you can see that’s not the actual email address. The “subject” is urgent; the body has typos and grammar errors, and asks you to click a link which is spoofed - hovering over the link reflects a different URL than what is show in the link itself.

Here’s an example of the body of a phishing email from Paypal:
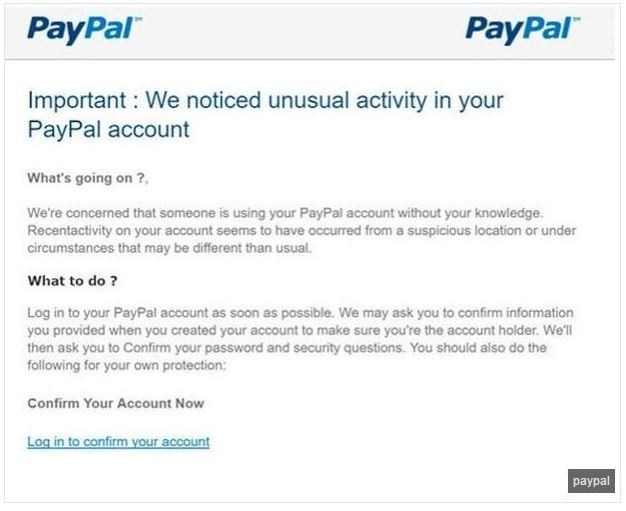
Notice that there are several grammatical mistakes and typos throughout this email message - the body tells you that you need to “take action now” by following the link, but doesn’t go into detail about any specific issue or mention you by name or include any of your account details for verification.
Some phishing emails are intended to gather information and send it back to scammers. While this type of phishing email doesn’t have an attachment or link, it serves to collect data - if someone replies to this message, the scammer who sent it will collect their email information and signature, and can use it to launch another spoof campaign.
CONSEQUENCES OF PHISHING
If you are victimized by a phishing email (by replying to it, or downloading a malicious attachment), you may not observe issues right away, and some may just barely be noticeable to you.
Some of the following things may occur:
- Redirection to websites that you didn’t intend to go to
- Frequent pop-up ads
- Computer Slowdown
- Your “sent” or outbox may contains messages you didn’t send
- Your passwords change without you changing them
- a sudden increase in spam mail
If you notice the warning signs above and believe you may have clicked a malicious link from a phishing email:
DO NOT turn off your computer. Some malicious applications don’t install fully until the next reboot/startup. Leave the computer ON.
DO disconnect your computer from the Internet.
DO call IT Client Services at 201-761-7800 immediately.
These signs may indicate you have acquired a malicious application or virus, and may be not only affecting the security of your own personal computer and applications, but others as well! Self-propagated malware attacks may access your logged in email accounts, and send out the phishing message to people on your contacts list.
Some attempts at phishing will not be accompanied with malicious software of files, but will instead ask you for personal and confidential information via the email itself, or through a link, redirecting you to a “spoofed” website.
Be careful when providing confidential, personal information online - always check to make sure the website is secured, has trusted certificates and is up to date. If you are visiting a website that is asking for confidential information, go there through a known portal, rather than through a direct link sent via email. For example, if you get an email that comes from your bank asking you to log in to confirm your account details, if you suspect phishing, don’t click the link in that email - just go to the bank's website the way you normally do to log in.
Once you are on a website asking you for confidential information, make sure it is secured - it should start with “HTTPS” (it will have a little “lock” next to the URL bar - clicking on this generally lets you find out about the security of the website and it’s certificates.)

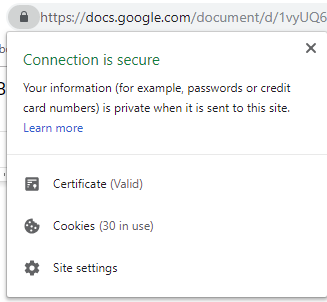
FYI: Most companies will NOT ask you to provide confidential information via email.
SAFE ONLINE SHOPPING DURING THE HOLIDAY SEASON
As the holidays approach, more and more people are taking advantage of online deals and promotions and performing their holiday shopping online. In the midst of the holiday shopping season, cyber criminals are actively perusing your confidential and personal information. Here's some resources offering best practices on how to avoid becoming a victim of holiday shopping season cyber crime:
REMEMBER: THINK BEFORE YOU CLICK THAT LINK, and report all suspicious activity to IT Client Services!